The Bad News:
Security attacks and cyber criminals target every business of every size. At this point, there is no 100% guaranteed protection against malware, ransomware or phishing attempts. In 2015, there were nearly 2,500 known complaints of ransomware reported to the FBI, amounting to $1.6 million in losses.
The Good News:
Every single user in your organization can play a part in fending off these kind of security threats. With the proper vigilance, awareness and IT security practices in play, your business can be protected to its best ability.
Since all it takes is one user in the organization to click on an infected link or attachment to fall victim, now is the time for every person in your organization to increase their cyber intelligence. In an effort to best protect your network, we’ve included our top 3 tips users in your organization can begin practicing today:
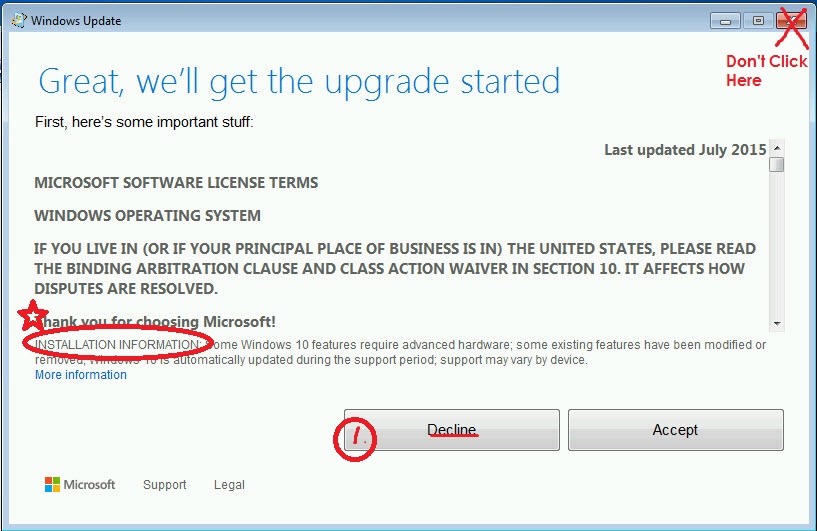
- Safely Exit Out of Unwanted Pop-Ups. Your popup blocker should be enabled, but at times you may still encounter advertisements or pop-up windows as you browse the internet. Do not click inside these windows as some of the buttons may have been reprogrammed by cyber criminals. Even legitimate Windows warnings or prompts for updates have used tricky tactics to get you to consent to updates when your intentions are to simply close the window. Read carefully any messages that just pop-up on your screen. Hover over links prior to clicking them to discover the intended redirect. When in doubt, use “Alt+f4” (terminate command) to safely exit out of unwanted pop-ups.
- Assume Public Wi-Fi is Not Secure. Hackers can easily set up a free accessible Wi-Fi network that looks like a legitimate source. Verify via signage or staff when connecting to Wi-Fi in a public space. Any banking or exchange of sensitive information should not be done while on a public connection. Use your cellular data if such transactions need to take place. You should also turn off file sharing and turn on your Windows firewall when connecting to a public network, if it is not already activated.
- Inspect All Links, Attachments and Any Clickable Object Carefully. Malvertising involves compromising an advertiser’s network by embedding malware in ads that get delivered through web sites you know and trust. Such malware attacks have proven successful even on hugely popular websites like that of New York Times and BBC. Hovering over any link or clickable object should result in additional information that pops up either to the side of the object or in the lower left hand corner of your monitor. This additional information should let you know where the object is redirecting you to, although a good cyber criminal may spoof this as well. When on a suspicious site, verify the the link will bring you to where you intend, by typing in the link on a new browser page directly instead of clicking on the link. Links that come in through your email can be copied and pasted into a virus scanner to ensure its authenticity. Be sure to have in place ad blockers to block malicious ads, as well as patching know browser security holes in order to further protect your internet browsing.
Things to Consider.
If users are the #1 security vulnerability in your business, than user training and security awareness is the #1 strategy to combat attacks. Applying these tactics on an ongoing and consistent basis will ensure security vigilance is at the forefront of everyone’s mind. Targeted campaigns can be sent out to all users to test your employees ability to detect phishing attempts. Scheduling a security awareness session with Compulite, may also prove helpful. Taking the time to discuss with your team the impact of malware and how attacks are being deployed against your organization can go a long way in combating security threats. Our security awareness session will also cover strategies every user in your organization can beginning using immediately to better protect your business data.