Ransomware is a threat to everyone in your organization. Businesses today are under constant attack from various security threats. It’s important that every user connected to your network understands how they are being targeted. When the impact ransomware could have on your business is understood, end users and your IT service provider can work together to provide the best protection.
Every User in Your Organization is at Risk.
Phishing attempts and hackers are ever-growing, ever-evolving circumstances that are Compulite’s top priority to circumvent and protect our clients against. Common security threats facing organizations today include: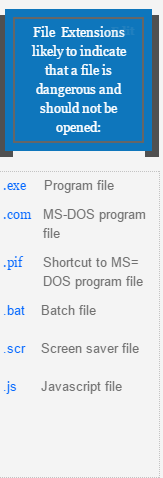
- Phishing: an attempt to bait a user to voluntarily release sensitive information (such as usernames, passwords, credit card numbers, etc.)
- Hacking: when your system has been exploited and access has been gained to something the hacker should not have access to (i.e., the server, company’s website, etc.)
- Malware: a term used to cover a variety of intrusive software, viruses, spyware or other malicious programs that can get installed onto your computer or device without your consent.
- Ransomware: a type of malware that restricts access to the infected system and demands payment of a ransom to remove the restrictions.
IT service providers should be taking preventative measures to help protect your network. Blocking zip files and other file extensions that come as an attachment within your e-mails is common best practice. Certain antivirus tools like Symantec Endpoint should also be installed to alert of any e-mail, file or internet threats.
All Users Need to Be Vigilant.
Since there is no way to guarantee complete protection from these events, it is important that all users do their part to protect the work environment as well. Users should be vigilant when you receive e-mails with links or attachments—even if it comes from a contact you recognize.
Any message that requests money or wire transfers over e-mail, prompts you to take “Immediate action” or implies a sense of urgency, should be inspected carefully. We have recently seen an increase of attachments named “Resume” or “My Resume” making it through filters. If a document called “Resume” is received in your inbox without a cover letter, or without being addressed to the appropriate person, do not open it.
Scan Files and URLs Before Opening.
If you encounter a suspicious file or URL via e-mail or when browsing the internet, you may hover over the link you receive to see it’s intended destination. If the link (or attachment) looks suspicious, forward your IT service provider the information to verify the source.
Users can also try using their local antivirus program or VirusTotal to scan it. VirusTotal is a free online service backed by Google that will scan a file or URL against numerous commercial antivirus providers giving you a recommendation of whether the file or web page is infected or not. It is not a complete guarantee that your document is clean of any malware but it’s a good place to start. If any malware is detected in your file, delete it from your system.
Reliable Backups May Not Provide Protection.
In the past, organizations that were being asked for ransom by hackers, could make the decision to ignore the threat if they had a reliable backup plan in place. However now hackers have adjusted their attacks and promise to leak sensitive business data to the public unless payment is received.
Ransomware collected $325 million (USD) in 2015 alone. The University of Calgary, a local Ottawa charity, and the Ottawa Hospital are recent vicitims of ransomware. With computer security researcher, McAfee, calling ransomware the biggest security threat of 2016, it will require every user to do their part to combat the attacks.
